Unlocking Defense-in-depth: A Protection Beyond Traditional Formulae
As cyberattackers and their nuisance are getting complexer and more advanced, the time has come for the enterprises to evolve and prepare for potential threats that can cause irreversible damages. With technological advancements and security enhancements, firms usually remain prepared for rule-based attack vectors or borderline deep intrusions. However, the proximity of data repositories at fingertips combined with the exploding rise of innovative technologies have allowed cybercriminals to launch unprecedentedly notorious and near invisible attacks for targeted enterprises.
Companies around the globe spend an average time of 204 days sorting out cases of data breaches.
According to the HIPAA Journal, 83 breaches were attributed to hacking/IT incidents and 9,662,820 records were exposed in those breaches.
More than 90% of attacks reported by our customers involve data or credential theft in one way or another
The need of the hour for hence for organizations is to safeguard themselves from such advancing threats and recover quickly from any security incidents; embedding solutions like advanced threats management, zero day protection, anti phishing policies, exchange online protection, and more. However, one of the biggest challenges companies encounter on the face of such severe attacks is the unavailability of qualified resources to detect, decode, and respond to such sophisticated mal practices. Cybersecurity leaders are hence looking for trusted partners that can deploy innovative, modernized data protection methodologies, arrange dedicated extended security teams, and integrate state of the art technologies to relieve organizations of the continuous threat stress. Proactive monitoring, immediate discovery and detection, and automated response and remediations are must haves.
Advanced Threat Protection by Cloud4C: Powered by Advanced SOC Practices
Cloud4C, the world’s leading application-focused Cloud Managed Services Provider has also been famed for its globally advanced cybersecurity practices, cloud-native security expertise, and competency with in-depth cyber protection solutions.
With Advanced Threat Protection by Cloud4C, enterprises can shield their sensitive databases, IPs and hosted assets, accounts, networks, platforms, and apps from deep targeted hacks, intrusions not conforming to existing patterns, advanced malware and ransomware, and sophisticated phishing attacks. Build a unique cyber defense structure aided with advanced threat intelligence, AI-powered security solutions and a world-class SOC team acting as a 24/7 extended partner to your entire cybersecurity needs. With Advanced Threat Protection, gain the much needed, extensively deeper and intelligent shield led by a trusted and innovative cybersecurity team for your IT operations, beyond traditional anti-threat software and strategies.
Benefits: Why Must Advanced Threat Protection be part of your Enteprise Cybersecurity Arsenal?

Deploy dedicated cybersecurity software to gain protection against complex cyberattacks and threats

Gain deeper risk visibility of enterprise perimeters including infrastructure, networks, platforms, endpoints, applications, etc

Advanced monitoring for malicious activities, suspicious footprints, and potential threat susceptibilities or vulnerabilities

Accurately identify risks or breaches to lower false positives and alert stress on cybersecurity teams

Continuous discovery and patching of misconfigurations across the landscape

Smart prioritization of security incidents based on business and operational needs

Coorelation of vulnerabilities with endpoint ecosystems to extend protection end-to-end

Deploy advanced machine learning solutions to hunt and investigate risks, breaches, and threat patterns

Built-in remediation processes through unique integration with advanced Microsoft technologies and other world-class solutions

Seamless integration with unique threat management solutions: SIEM, SOAR, XDR, and more

Deploy advanced threat intelligence to map threat behaviours, tactics, procedures, and protocols for greater protection

Seamless integration with cloud-native solutions and cybersecurity platforms such as Azure Sentinel

Enable Zero Trust Security principles across enterprise landscape end-to-end including remote ecosystems

Deploy and connect with proprietary security automation technologies
Connect with our Advanced Threat Management Experts
High Level Snapshot:
What Can be Classified as Advanced Threats?
Advanced Malware and Ransomware
Trojans, Rootkits
Automated Phishing Tools
Crypto Mining Malware
Cloud Jacking
Zero Day Attacks
Advanced Persistent Threat (APT)
DDoS Attacks
Cloud4C Advanced Threat Protection:
Integration with World-class Security Solutions and Services
Microsoft Defender Advanced Threat Protection
- Attack Surface Reduction
- Endpoint Detection and Response
- Automated Investigation and Remediation
- Threat and Vulnerability Management
- Email and Attachments Protection
- Shareable Links Protection
- Spoof Intelligence
- Advanced Anti-phishing capabilities
- Threat Hunting
- Intrusion Management
- Database Activity Monitoring
- Advanced Threat Detection and Response
- Behavioural Analysis
- Data Forensics
- Advanced Threat Intelligence
- Threat Tactics, Behaviours, Procedures, Security Protocols
Azure Sentinel Integration
- Deep Threat Discovery
- Incident Detection and Analysis
- Cloud-native SIEM
- Security Orchestration and Response
- Vulnerability and Loopholes Scans
- Threat Detection and Investigation
- SIEM-SOAR Integration
- Threat Mitigation and Asset Recovery
- Data, Applications, Network Security
- Host Based Security System
- Identity and Access Management
- Next Generation Firewall
- Continuous Verification and Monitoring
- Threat Containment
- Automated Context Collection and Response
- Modernized Security Frameworks
Connect with our Advanced Threat Management Experts
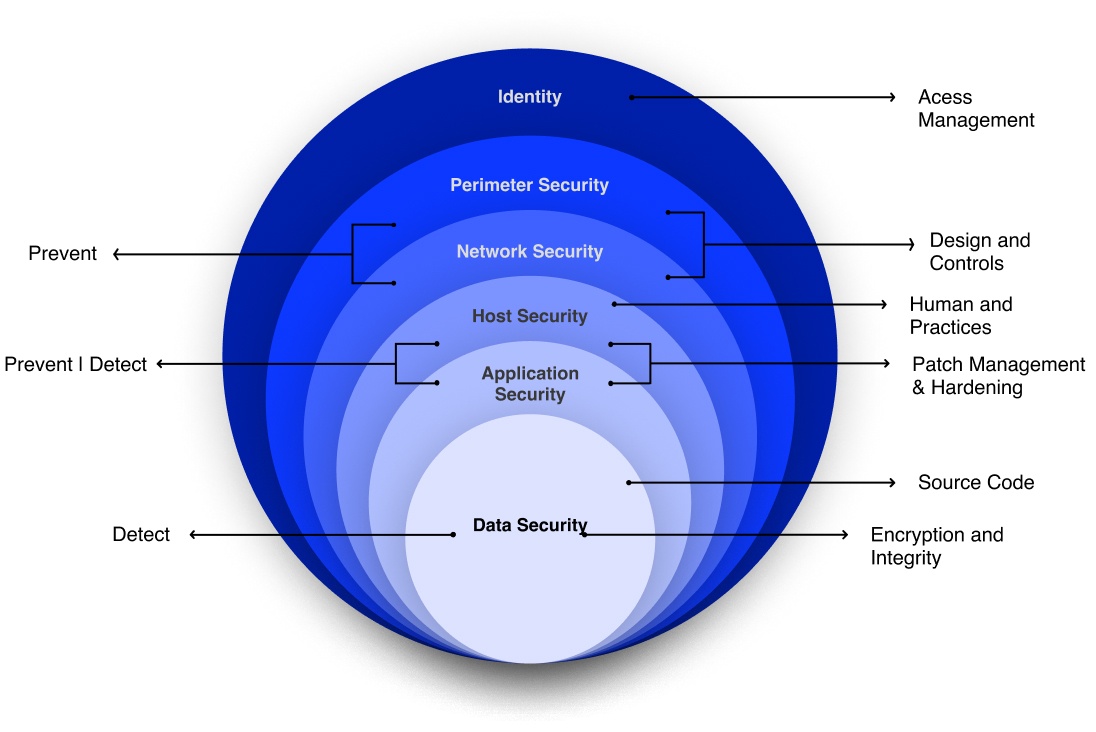
Cloud4C Defense-in-depth Map:
Powered by Advanced Threat Management
An Impact with Difference: Why Partner with Cloud4C for your Enterprise Cybersecurity Transformation?
World’s largest application-focused managed service provider with dedicated Managed Security Services and advanced managed Security Operations Center Offerings

10+ years expertise, 4000+ transformation stories across 25+ nations

800,000 EPS, 1400 HBS, 1200 UTMs, 7 Reg-tech Frameworks, 40+ Security Controls

2000+ cloud experts and a world-class security team with industry-leading certifications: Hyperscaler Security, Hyperscaler Platform, CISSP, OSCP, CEH, CHFI, Comp TIA Security

Proprietary, intelligent automation powered cybersecurity tools such as the Cloud4C Self Healing Operations Platform

Specialized SOC audit, compliance management expertise ensuring stringent, fail-proof governance and compliance with local, national, and international regulations

Security frameworks utilizing the MITRE ATT&CK, CIS Critical Security Controls, and more

Comprehensive 24/7 threat monitoring across the entire IT and cloud stack

Dedicated Cyber Security Incident Response Team with anytime, anywhere support and issue solving

Threat Intelligence powered by industry-leading platforms such as Microsoft, OSINT, STIX&TAXI, MISP, etc

Specialized expertise in deploying robust SIEM-SOAR for proactive vulnerability assessment and automated-accelerated incident response

Cloud-native security with multi-cloud support for leading cloud platforms: AWS, Azure, GCP, Oracle, IBM Cloud, etc
Advanced Threat Protection - FAQs
-
What is advanced threat protection?
-
Advanced Threat Protection is a solution that helps enterprises protect against complex malware or hacking attacks which usually target sensitive data and critical systems.
-
What is Microsoft threat protection?
-
The Microsoft threat protection helps enterprises identify the Microsoft defender for identify and Azure AD Identity Protection. It uses Active Directory signal to identify, detect and understand advanced threats, malicious actions and compromised identities.
Solidify your Enterprise Cybersecurity with Cloud4C
Talk to us



