The world will remember 2020 for n-number of negative reasons. But for CSOs and CISOs, 2020 unfurled a wave of massive cyberattacks that left them as well as the world shaken. The pandemic and its resultant rise in remote work made inroads for some of the most challenging attacks and data breaches in the history of cyber security. Let’s take a look at the impact of data or security breaches.
-
Alarming State of Cybersecurity in 2020-21
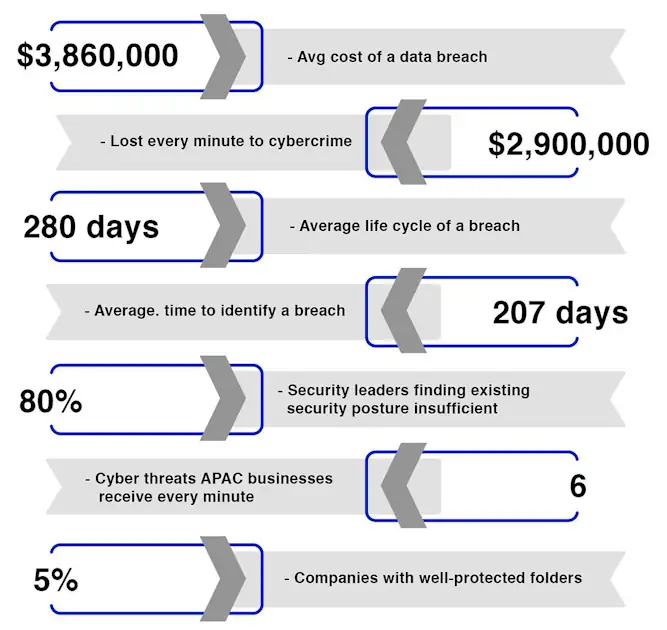
Not only were those attacks unprecedented in number but alarmingly sophisticated in nature too. From Marriott International, New Zealand Stock Exchange to Solar Winds or Twitter, each and every ransomware attack or data breach laid bare the vulnerability of cyberspace, making it evident even to the naked eye.
While a lot has been written, spoken, and debated about the key factors behind this sudden rise in cyberattacks, none of us would disagree that the success of these new-age attacks can be attributed to poorly managed/monitored infrastructure. Almost every business is making its leap to the cloud by migrating data centers. Add to that the phenomenal rise of IoT-enabled devices coupled with a lack of integration of cloud devices and the whole infrastructure managed by inexperienced security teams. Sounds like a field day for threat actors already?
One way to prevent enterprises from these intelligent attacks is identifying and responding to events and alerts in real-time a.k.a. Security Information and Event Management (SIEM). Today, businesses of all types and sizes, operating in this digital ecosystem, generate huge volumes of data. SMBs, on average, deal with approximately 47.81 Terabytes of data which is expected to double in a year and a half.
That’s where Azure Sentinel comes into the picture. Launched in February 2019, Azure Sentinel is an evergreen scalable cloud native SIEM and SOAR solution designed by Microsoft experts to help organizations collect and analyze diverse sets of data at scale to identify and protect data breaches and targeted attacks before they can do any harm. Within just a year, it made its way to the Forrester Research’s list of ‘Leaders’ in the Forrester WaveTM: Security Analytics Platform Providers, Q4 2020.
Hence, touted as one of the most intelligent security analytics for enterprises, Azure Sentinel combines the power of SIEM with its SOAR (security, orchestration, automation, and response) capabilities, making it an ultimate choice for security-conscious organizations who aim to improve their overall security posture. Built on Azure platform and powered by AI, this solution comes as a relief for enterprises who were so far struggling with building and managing their security architecture.
What makes Azure Sentinel so appealing?
|
Simplified Security Orchestration |
Built-in AI |
Automatic Response |
|
Easy Installation |
Seamless Integrations |
Deep Investigation |
The first step to on-board this solution is to connect all the security sources and data sources with it. Azure Sentinel comes with the opportunity of real-time integration of a bunch of Microsoft solutions including Microsoft 365 Defender, Office 365, Microsoft Defender for Identity, Azure Active Directory, Microsoft Cloud App Security, etc. Moreover, it’s built-in connectors offer the flexibility to connect non-Microsoft sources as well, securing your data sources end-to-end.
But how do you monitor all the connected data sources? Well, Microsoft has thought about that too. By integrating Azure Sentinel with Azure Monitor Workbooks, users can get a holistic view of all the data sources enabling easy monitoring, deriving insights across the data sources, and creation of interactive reports.
Another key advantage of this cloud-native SIEM solution is how it leverages the security orchestration and automation (SOAR) feature to simplify security orchestration. Built on the Azure Logic Apps foundation, the SOAR program offers scalable automated response for new emerging threats. Another automation feature, Automation Rules (still in preview), makes incident handling even easier. This feature allows users to automate several tasks without the need for any playbook. One can automatically respond to various analytics as well as control the order of actions, resulting in streamlined automation process across the otherwise-complex security workflows.
That’s how Azure Sentinel makes the lives of your entire security team easier—from the CISO to the analysts. It also improves your SOC’s (Security Operation Center) efficacy besides mitigating vulnerabilities at scale.

Key business benefits of Azure Sentinel
Cloud-scale data aggregation
Azure Sentinel, unlike traditional SIEMs, frees you from cumbersome tasks such as data collection, infrastructure setup, maintenance, and scaling. As it is built on the Azure platform, you also get to enjoy unlimited cloud scaling and speed for your enterprise security needs.
Faster data normalization
SIEMs tend to normalize the aggregated data in different formats as per your need, ensuring consistent log management and easy correlation. The Azure Monitor feature in Azure Sentinel is designed to normalize millions of data records in seconds. Azure Monitor is built on a smart and scalable log analytics DB that consumes as much as 10PB of data every day.
Compliance
Today, it’s impossible to establish or run a business without adhering to multiple regulatory compliances such as HIPAA, PCI-DSS, or SOX. SIEM solutions help enterprises meet these stringent compliance requirements by providing a mechanism that makes deploying log collection infrastructure fast and easy. With this mechanism in place, businesses can easily access recent log data as well as archive or retrieve old log data.
Proactive threat hunting
With Azure Sentinel, enterprises get the opportunity to bring all their events across a hybrid environment into a single glass pane in the cloud which makes the solution a SIEM-as-a-service model. Azure Sentinel takes threat hunting to a whole new level with its predictive analytics capabilities. As compared to the Azure Security Center, Azure Sentinel identifies threats much proactively. Hence, events are detected even before they occur.
Out-of-the-box detection
The aim of connecting your data sources to Azure Sentinel is to get event alerts. That’s where the solution’s out-of-the-box templates come into action. These built-in templates, based on known threats, suspicious activity chains, allow you to create or customize threat detection rules.
Advanced multi-stage attack detection
One of the latest attack techniques from the kitty of these constantly evolving cyber attackers is multi-staged attacks—security breaches performed at different stages of the kill chain. Azure Sentinel, using its ML-powered fusion technology, can easily identify any suspicious activities and anomaly combinations and deter such attacks.
How to get started?
While getting started with Azure Sentinel is quite a simple task, it’s important to assess your current security architecture to identify all the capabilities, technologies, processes, dependencies for a seamless journey to enhanced threat protection. A thorough assessment ensures that every new solution gets easily integrated into the existing system. The next crucial step is cost analysis which is required for change management. Once the solution is deployed, it needs to be regularly monitored to reap maximum benefits.
Cloud4C, an Azure Expert MSP, helps leading government entities, banks and financial institutions, real estate majors, large manufacturers as well as retail and communications leaders across the globe strengthen and simplify their security environment with our Managed Security Services for Azure Sentinel.
In order to allay the fears of embracing a cloud SIEM and SOAR tool, give enterprises hands-on experience and understanding on how to use Azure Sentinel, discover and mitigate threats, we conduct Proof of Concept workshops. In the workshop, we answer all the queries, demonstrate advanced threat modeling, and showcase how post Sentinel’s deployment, a hawk eye’s view of their environment, possible threats, and how to intelligently mitigate them will be ensured.

For more information, get in touch with our Azure Sentinel experts.










