Table of Contents:
- Introduction: Traditional SOC is dead
- How is a SOC Structured?
- What are the problems with security operations centers?
- What is a Next-Gen SOC?
- Traditional SOC vs Next-Gen SOC- Why is the Latter Better?
- How to Build a Modern SOC- Follow these 5 Best Practices
- Adopt Best-in-Class Managed SOC Services with Cloud4C
“Traditional SOC is dead!"
When Cloud4C interviewed Mr. Sachin Rathi, (Director, Industry Solutions & Strategic Initiatives at Microsoft), he emphasized replacing legacy security solutions with advanced SOC services to thrive securely in a dynamic threat landscape. Given that a new security breach takes place every 39 seconds, he is not completely wrong.
Is Traditional SOC Going Obsolete Soon?
With 77% of organizations adopting Security Operations Centre (SOC) solutions and services, it has been found that 50% find SOC solutions to be ineffective against next-gen, unplanned threats. Think about it. There is a hospital running with a traditional SOC system. A PHI exposure in the imaging equipment led to a delay in surgeries, causing frenzy among doctors and patients alike. Their existing SOC solution overpassed this threat that ultimately put the patients' lives at risk. The good news is that this is just fiction; however, it won't take a few bad decisions to turn this fiction into a disastrous reality
For solidifying cyber defense centers in mission-critical environments, security models need to evolve rapidly. Here comes the alternative: next-generation SOCs. They provide a more integrated and sophisticated approach to incident response, threat identification, and mitigation.
This blog will take you through the ins and outs of advanced SOC models, why they are the need of the hour, and what makes them more effective than their counterparts. Before that let's understand how a traditional SOC framework works and why it needs an evolution in the first place.
How is a traditional SOC Structured?
In a traditional Security Operations Center (SOC) framework, the analysts are categorized into a tiered system called L1, L2, and L3 based on their experience and skillset.
SOC Engineering: SOC engineering is responsible for deploying, monitoring, and managing tools effectively. For instance, a security incident and event management (SIEM) tool needs to be implemented to reduce the incidences of false positives and tackle breach events. Typically, the SOC engineering team is well-versed with two or more SOC tools such as DLP, SIEM, and carries 5-7 years of experience in threat detection (L3).
Incident Analysis & Triage: When an alert is sent by a tool, it's important to assess and rank it based on potentialities. The L1 and L2 analysts implement the triaging process through techniques called playbooks to analyze the nature of the security alerts.
Incident Response: After their initial analysis, L1 and L2 analysts escalate the incident to the Incident Response (IR) team. The IR team is responsible for determining the impact of the security alert and recommending remediation measures accordingly. The scope of the IR team, however, is not limited to technicalities. They need to view cybersecurity incidents holistically taking into legal and PR perspectives. Drills are an effective tool to test and enhance incident management responses. They are conducted periodically and mostly unannounced so that the IR process remains proactive. L3 analysts are very experienced as they majorly analyze current and future data security trends and study new threat actors and vectors in detail.
| Related Content | Do you want to know how to build strong cyber defense centers? Read our blog on bullet-proofing your Security Ops with Red Teams, Blue Teams, and Purple Teams |
Challenges with Traditional Security Operations Centers?
Traditional SOC models are broken. Here's why:
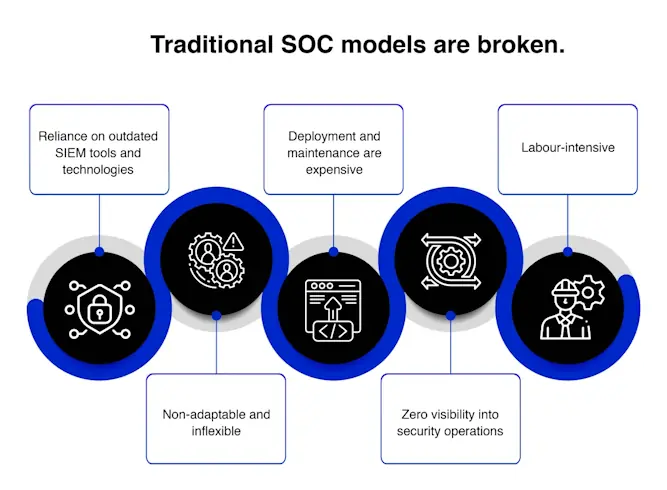
Given the limitations of traditional SIEM tools, a single orchestrator is the need of the hour that combines security alerts, assesses their source, and remediates them in real-time.
Enter next-gen SOC.
Remodeling Security: What is a Next-Gen SOC?
Next-Gen SOC model is an upgrade to address the limitations posed by traditional SOCs. In other words, its core objective is to enhance the existing cyber defense mechanism of an organization through specialized tools and techniques, involving deep analytics and AI. While deploying tools like Network Traffic Analysis (NTA), Endpoint Detection and Response (EDR), Anomaly Detection, the main difference between the two SOC models is the addition of the new step: Threat Intelligence and Hunting.
Threat Intelligence (TI): Threat Intelligence augments the ability to identify sophisticated security threats. It is broadly classified into three stages: Strategic, Tactical, and Operational. Strategic threat intelligence provides a granular view of the motives of cyber criminals to make long-term decisions around security programs. On the other hand, tactical threat intelligence offers in-depth information into specific threat vectors, IOCs, and TTPs (Tactics, Techniques, and Protocols) of threat actors. Operational threat intelligence offers insights into day-to-day security activities to accelerate real-time detection.
Through this, it amplifies the existing SOC's capabilities to build a strong foundation for continuous monitoring and threat detection. For instance, Indicators of Compromise (IOC) is an element of digital forensics that highlights any malicious behavior and upgrades the accuracy of detection, monitoring, and response activities. In addition, integrating TI with the current SIEM tools minimizes false positives. Standardized formats such as STIX and TAXI have been created to publish threat intel reports.
Threat Hunting: Taking threat detection to the next level, hunting leverages big data and analytics to identify potential threats based on logs and historical data. Either using hypothesis or IOC, analysts simulate attack scenarios and note down potential threat actors. Based on this, a data scientist develops an algorithm that helps to discover the sources of these vectors and tests this algorithm on historical data and logs. Usually, hunting is useful for detecting slow and low attacks that are overlooked by SIEM tools. A data scientist along with the analyst creates an algorithm to identify traces of potential attacks using these vectors.
| Related Content | Looking to enhance your intrusion system detection? Read our blog on different kinds of penetration testing and how to best combat them. |
Traditional SOC vs Next-Gen SOC- Why is the Latter Better?
Advanced Threat Detection: Next-Gen SOC uses a host of modern technologies such as intrusion detection systems, antivirus software, and firewalls to detect anomalies in organization's networks and systems. Furthermore, it detects external sources such as the dark web and social media for any potential threats.
Other than this, using AI and ML helps in assessing huge volumes of data sets for any potential vectors that may, otherwise, get overlooked through old SIEM solutions. Using threat intelligence platforms and malware analysis technologies can gather data and malware samples from open-source intelligence and close feeds. This helps in giving insights into the tactics, techniques, and procedures (TTPs) used by cybercriminals.
Advanced Response and Remediation: Typically, four steps are involved in the response and remediation process of advanced SOC services:
- Containment: Taking substantial preventive measures such as blocking harmful traffic and blocking infected systems from the network
- Eradication: Removes the threat by either destroying the malware or restoring back-up data.
- Recovery: Recovers data and systems to their pre-attack state
- Feedback: Documents and publishes a post-incident review for recommendations and areas of improvement
Unified cybersecurity posture overview: By integrating SIEM tools and incident response platforms, next-gen SOC offers a unified view into the cybersecurity posture and a centralized interface for collaborating their response efforts with other stakeholders.
SOAR is deployed to automate rudimentary security tasks, such as sending alerts to the designated security professional quarantining damaged systems. It can ensure seamless collaboration and communication among stakeholders through video conferencing and chats.
Security Automation: There are two kinds of automation, namely workflow automation and rule-based automation. The former involves monitoring the status of a security breach or escalating threat incidences. On the other hand, the latter involves automating tasks such as isolating infected systems or preventing bad traffic against a set of pre-determined rules and standards.
| Related Content | How to enhance your security incident and event management? Read our blog on automating incident management with Azure Sentinel |
How to Build a Modern SOC- Follow these 5 Best Practices
Distinguish the security tasks that need automation
In a traditional SOC, security analysts deal majorly with known threats or rule-based threats, which prevents them from focusing on dealing with threat intelligence and hunting. Repetitive tasks eat up too much of their time which is where automation is duly required. By automating the identification of common and less advanced threats, analysts can focus on combating targeted attacks and threat hunting.
Using the SOC Playbook Wisely
Given the huge volumes of data generated through firewalls and end-point security systems, analysts in traditional SOC have to analyze each data set manually. Processing security alerts from multiple network sources is indeed a task at hand. One smarter way is to integrate data from different sources into a centralized dashboard that can give an overview of threats that need automation or necessitate human intervention. Automate the simple processes laid down in the SOC playbook for identifying low-level threats.
Don't overburden SOC analysts
Meanwhile, in conventional SOC, security analysts would spend hours manually assessing the source of the threat. Automate the process with threat intelligence. Security alerts are sent off quickly to the security personnel within 5 seconds of identifying this threat and the infected system is quarantined from the network.
Support cloud-native tools
38% of SOCs today are leveraging public cloud analytics with 44% of them adopting a hybrid cloud approach. Out of which, a certain segment prefers either of the two options including integrating SIEM tools with cloud-native tools or replacing legacy SIEM technologies with cloud-native solutions rather than just lifting and shifting their on-prem security services. For managing the security cloud workloads, cloud security analytics enhance the scope of real-time threat detection, threat intelligence, risk monitoring, and response management.
Establishing open architectures
To make next-gen SOC work to the best of its capabilities, organizations require a common security analytics and operations platform architecture (SOAPA) to collate data from various security platforms. This open architecture should be integrated with layered SIEM, SOAR features, and user and entity behavior analytics (UEBA). They serve as unified interfaces that gather data from additional layered analytics tools so that analysts don't need to switch from one interface to another interface to monitor logs and networks.
Adopt Best-in-Class Managed SOC Services with Cloud4C
Implementing next-gen SOC is difficult on two major fronts. Firstly, enterprises need to understand how and what advanced SOC tools are to be integrated with the base SIEM platform. These could range from UBA, EDR, to anomaly detection, and response automation. Secondly, there is a scarcity of professionals with diverse skills that can assist with enhancing visibility, IR, and threat detection capabilities in real-time. Such intricate challenges require the extended expertise of a managed SOC services provider.
Cloud4C offers advanced managed SOC services that unify security operations such as threat monitoring, investigation, detection, incident, and response management across the cloud infrastructure. Acting as a single point of contact, our dedicated security experts help in embedding tools such as SIEM-SOAR, Threat Intelligence, Governance Risk and Compliance Systems (GRC), Database Scanners, Intrusion Prevention Systems, MITRE ATT&CK, User and Entity Behavior Analytics (UEBA), Endpoint Detection and Response systems.
In addition, automate your security management with our Self-Healing Operations Platform (SHOP) to gain continuous 360-degree monitoring of security infrastructure, identify anomalies, and enable immediate remediations by deploying a set of home-grown AI/ML tools and clustering and regression models. With SHOP, predict and patch probable anomalies and risk-proof your mission-critical operations even before a breach occurs, a.k.a predictive healing and preventive maintenance.
Want to gain compliant, automated, and AI-powered platforms to deploy the best of security capabilities? Visit our website or get in touch with our representative today.







